Replace ESXi Certificate
The ESXi host uses automatically generated certificates that are created as part of the installation process. These certificates are unique and make it possible to begin using the server, but they are not verifiable and they are not signed by a trusted, well-known certificate authority (CA).
Using default certificates might not comply with the security policy of your organization. If you require a certificate from a trusted certificate authority, you can replace the default certificate.
Note
If the host has Verify Certificates enabled, replacing the default certificate might cause vCenter Server to stop managing the host. If the new certificate is not verifiable by vCenter Server, you must reconnect the host using the vSphere Client.
ESXi Certificate is generated by ESXi Internal CA using openssl. You can find the certificate files that ESXi server uses in /etc/vmware/ssl directory.
~ # ls -l /etc/vmware/ssl/ -rw-r--r-- 1 root root 1411 Apr 13 00:17 rui.crt -r-------- 1 root root 1675 Apr 13 00:17 rui.key ~ #
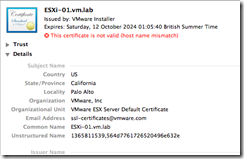
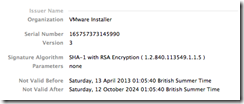
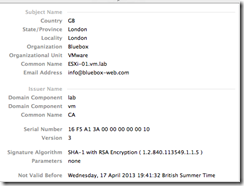
You can view the certificate information, notice that it is a self-signed certificated.
Re-generating new self-signed ESXi Server Certificate using ESXi internal CA
You can re-generate ESXi Server certificate using ESXi internal CA, i.e openssl, if the certificate is expired, compromised or configured with incorrect date.
Step 1
You will need to access ESXi Shell. if you want to use SSH, then enable SSH on ESXi Server, then put the ESXi Server into the maintenance mode.
Step 2
Access ESXi Shell then rename the certificate file and private key file.
/etc/vmware/ssl # mv rui.crt old.rui.crt /etc/vmware/ssl # mv rui.key old.rui.key /etc/vmware/ssl # ls -l -rw-r–r– 1 root root 1411 Apr 13 00:17 rui.crt -r——– 1 root root 1675 Apr 13 00:17 rui.key
Step 3
Regenerate a new certificate using generate-certificate command and verity that the new certificate file and private key file are generated.
~ # /sbin/generate-certificates ~ # ls -l /etc/vmware/ssl/ -rw-r--r-- 1 root root 1411 Apr 13 00:17 old.rui.crt -r-------- 1 root root 1675 Apr 13 00:17 old.rui.key -rw-r--r-- 1 root root 1407 Apr 13 03:44 rui.crt -r-------- 1 root root 1675 Apr 13 03:44 rui.key ~ #
Step 4
Restart ESXi Server Management agent via DCUI under Troubleshooting Option or use /sbin/services.sh restart command via CLI
Step 5
Now ESXi Server has a new certificate as you can see from the Finger Print. Be aware that this is still a self-signed certificate.
Replacing ESXi Server Certificate with CA signed Certificate
The previous instruction was to regeneration a new self-signed certificate. This demonstration walk you through how to use your own CA for ESXi Server certificate.
In this demonstration, I will be using Windows 2003 R2 x64 based enterprise CA. You can use any CA you wish.
vSphere products are shipped with openssl. you can use openssl in ESXi server to generate a certificate request. For this demonstration, I installed OpenSSL 0.9.8y on my vCenter Server (Windows 2008 R2 Datacenter).
Step 1 (Optional)
Edit openssl.cfg under C:OpenSSLbin. This will set the default option for certificate requests. I only changed the following values.
[ req_distinguished_name ] countryName_default = GB stateOrProvinceName_default = London LocalityName_Default = London 0.organizationName_default = Bluebox organizationalUnitName_default = VMware emailAddress_default = info@bluebox-web.com
Step 2
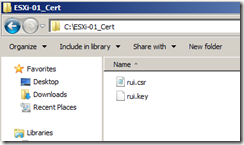
Make a folder under to store ESXi server Certificate files, then generate a private key to be used by ESXi Server certificate.
C:OpenSSLbin>mkdir c:ESXi-01_Cert C:OpenSSLbin>openssl genrsa -out c:ESXi-01_Certrui.key Loading 'screen' into random state - done Generating RSA private key, 512 bit long modulus .++++++++++++ .............++++++++++++ e is 65537 (0x10001) C:OpenSSLbin>
Step 3
Generate a certificate request for ESXi server. You will need a hostname for the ESXi Server here.
C:OpenSSLbin>openssl req -new -key c:ESXi-01_Certrui.key -out c:ESXi-01_Certrui.csr Loading 'screen' into random state - done You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [GB]: State or Province Name (full name) [London]: Locality Name (eg, city) []:London Organization Name (eg, company) [Bluebox]: Organizational Unit Name (eg, section) [VMware]: Common Name (e.g. server FQDN or YOUR name) []:ESXi-01.vm.lab Email Address [info@bluebox-web.com]: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: C:OpenSSLbin>
Step 4
Confirm that Certificate request is generated.
Step 5
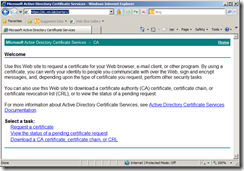
As I am using Microsoft Windows CA, I will be using Certificate Service Web Enrollment page via https://<IP-Address-of-CA>/certsrv. Request a certificate via
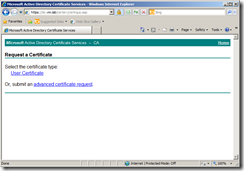
1. Request a certificate
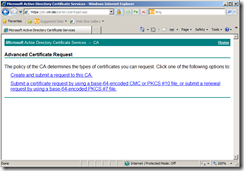
2. advanced certificate request.
3. Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file.
Step 6
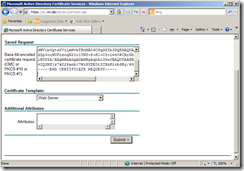
Open the certificate request file in a text editor such as Notepad, and copy all text output, then peste it in the box. Make sure to select Web Server from Certificate Template Option, then click Submit.
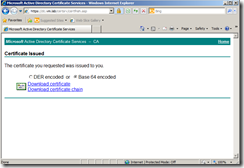
Step 7
Download a issued certificate with Base 64 encoding, and save it on the folder created earlier, I named it rui.cer.
Step 8
ESXi server requires x509 based certificate, so change the format of certificate file using the command below.
C:OpenSSLbin>openssl x509 -in c:ESXi-01_Certrui.cer -out c:ESXi-01_Certrui.crt
Step 9
Verify that the file is created.
Step 10
Then you will need to transfer the new certificate to ESXi Server using SCP. I used FileZilla for this. Make sure to overwrite existing files (rui.key and rui.crt) or rename in /etc/vmware/ssl directory them prior to this.
Step 11
Restart ESXi Server Management agent via DCUI under Troubleshooting Option or use /sbin/services.sh restart command via CLI
Step 12
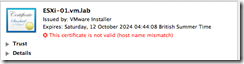
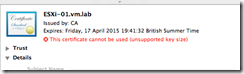
Now verify that the new certificate is used by ESXi Server.